Understanding the IP2 Network: What It Actually Means
The IP2 Network is a term that can refer to two very different things, and this confusion trips up many people searching for information online.
Quick Answer – IP2 Network refers to:
- Technical Network: A decentralized, privacy-focused communication system (often referring to I2P – Invisible Internet Project)
- Community: The Ice Poseidon 2 streaming community and their events like #RV6
- Core Features: Peer-to-peer architecture, encrypted tunnels, censorship resistance
- Key Benefit: Puts data control back in users’ hands without centralized servers
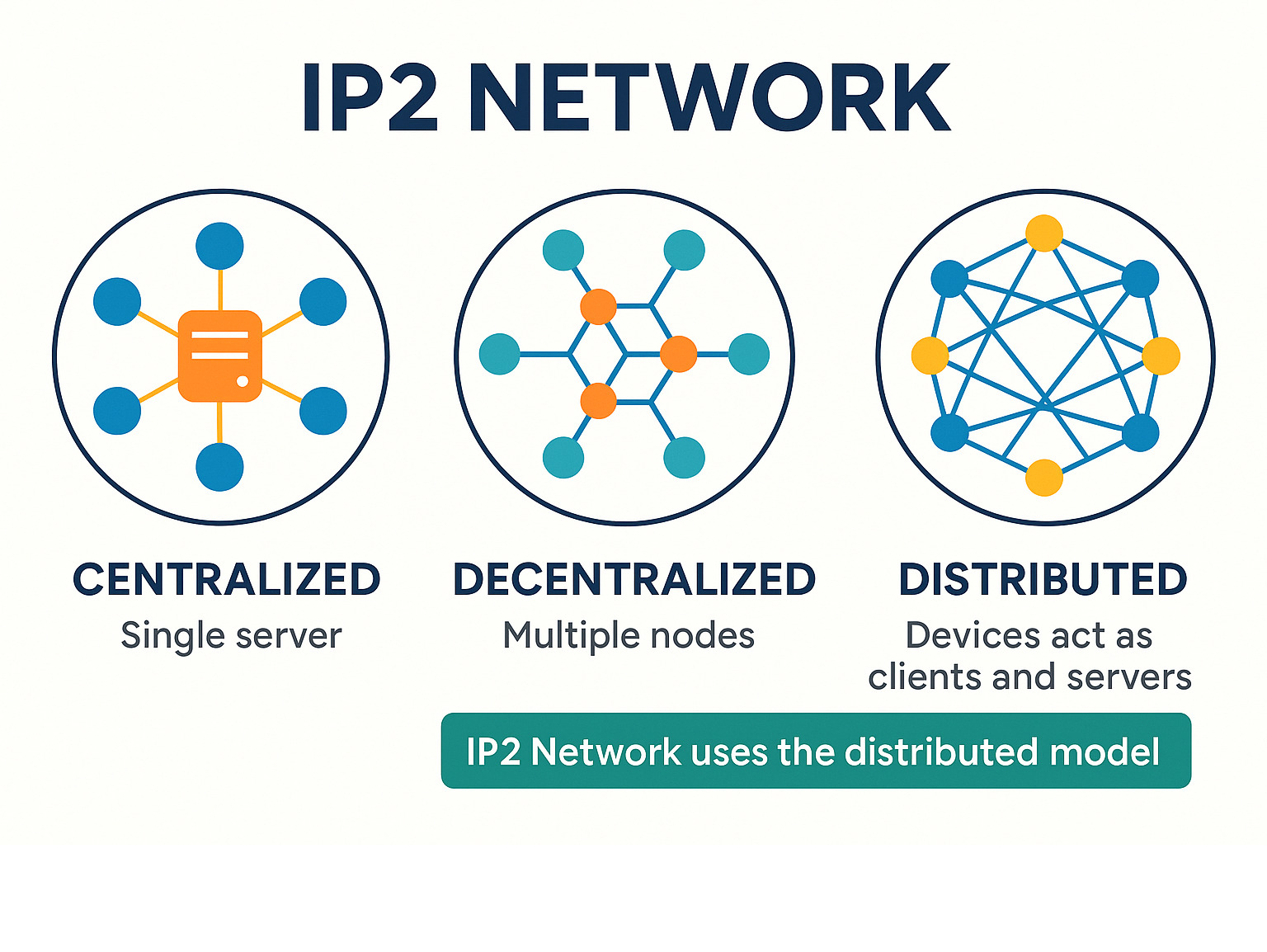
The technical IP2 Network represents a fundamental shift in how we think about internet communication. Unlike traditional networks that route your data through centralized servers, IP2 Network creates direct, encrypted connections between users.
This matters because every device becomes a node in the network. Your data doesn’t pass through corporate servers that can track, store, or sell your information. Instead, it flows through encrypted tunnels that hide both your identity and your destination.
The network uses what researchers call “garlic routing” – a method that bundles multiple messages together and sends them through different paths. This makes it nearly impossible for anyone to trace your online activity back to you.
For travelers and food enthusiasts who value privacy while researching destinations, sharing reviews, or connecting with local dining communities, understanding these privacy-focused networks becomes increasingly important in our data-driven world.
Quick ip2 network terms:
What is the IP2 Network? A Deep Dive into Decentralized Communication
Think of the IP2 Network as the internet’s answer to a growing question: What if we could communicate online without anyone watching? It’s a decentralized, privacy-first network that hands data control back to you, the user. No corporate middlemen, no central servers collecting your information, no surveillance backdoors.
This isn’t just another tech buzzword. The IP2 Network represents a fundamental shift in how we think about digital communication. When you send a message or browse online through traditional networks, your data bounces through servers owned by companies that can track, store, and even sell your information. The IP2 Network cuts out these middlemen entirely.
Instead, it creates direct, encrypted connections between users through a peer-to-peer (P2P) architecture. Your laptop in that cozy café, your phone while exploring a new city’s food scene, even your tablet while researching restaurant reviews – each device becomes a node in this vast, interconnected web. No single company owns or controls the network.
The beauty lies in its censorship resistance. When information can vanish based on location or politics, this network ensures your voice stays heard. It’s built for free expression and unrestricted information flow.
When we talk about the technical IP2 Network, we’re primarily referring to the Invisible Internet Project, or I2P Anonymous Network. I2P creates a fully encrypted private network layer that protects both your activity and location. All traffic stays internal to the I2P network, never touching the traditional internet directly. This means the server can’t see you, and you can’t be traced back to the server.
The Core Technology Behind the IP2 Network
The IP2 Network runs on some seriously clever technology. Its node-based architecture means there’s no central server to hack or shut down. Your data spreads across thousands of connected devices, creating a network that’s both robust and nearly impossible to break.
The real magic happens with unidirectional tunnels. Unlike normal internet connections where data flows both ways on the same path, the IP2 Network uses separate encrypted tunnels for each direction. This makes tracing your activity like trying to follow a ghost through a maze.
End-to-end encryption protects every bit of data as it travels. This isn’t basic password protection – it’s military-grade security that keeps your information locked away from prying eyes.
The network also uses dynamic routing powered by AI-based intelligent systems. Think of it as having the world’s smartest GPS for your data. It constantly finds the fastest, safest routes while avoiding traffic jams and roadblocks. This smart routing bypasses geographical restrictions and surveillance attempts.
All of this works through garlic routing – the network’s secret sauce. Like Tor’s “onion routing,” garlic routing bundles multiple encrypted messages together (like cloves in a garlic bulb) and sends them through different paths. Each node only sees enough information to pass the message along, never the full picture. It’s like having a relay race where each runner only knows the next person in line.
Distinguishing “IP2”: The Network vs. The Community
Here’s where things get confusing, and we need to clear the air. The technical IP2 Network (the I2P privacy system we’ve been discussing) is completely different from the “IP2 Network” streaming community you might find online.
The streaming “IP2 Network” grew out of the Ice Poseidon fanbase. When some fans wanted more controversial content than the original streamer provided, they created their own community called “IP2” (Ice Poseidon 2). This group organizes events like #RV6 – real-life streaming adventures that started with Ice Poseidon but eventually became their own thing.
These are different entities that just happen to share similar names. When we talk about privacy, encryption, and decentralized communication, we’re discussing the technical IP2 Network (I2P). The streaming community is entirely separate.
It’s like having two restaurants named “Joe’s” in different cities – same name, completely different experiences.
How the IP2 Network Differs from IPv4/IPv6
For decades, the internet has run on traditional protocols like IPv4 and IPv6. These are basically the postal system of the internet – they make sure your digital mail reaches the right address. IPv4 is running out of addresses (like a city running out of street numbers), while IPv6 provides billions more addresses to solve this problem.
The IP2 Network works differently. It’s not trying to replace IPv4 or IPv6. Instead, it operates as a network layer on top of the existing internet infrastructure. Think of it as adding a secure, private tunnel system over the existing highway network.
Here’s the key difference in focus:
- IPv4/IPv6: Getting data from point A to point B efficiently
- IP2 Network: Getting data from A to B privately and anonymously
The traditional protocols are the highways. The IP2 Network is about traveling those highways invisibly. It offers backward compatibility with current systems, so you don’t need to rebuild the entire internet to use it.
For food travelers and dining enthusiasts who value privacy while researching destinations or sharing reviews, understanding this distinction helps explain why the IP2 Network matters for secure communication. For more detailed information about network infrastructure and the critical transition happening in internet protocols, you can explore resources like iproutes.net.
How the IP2 Network Compares to Other Privacy Tools
When you’re exploring ways to protect your privacy online, you’ll quickly find that the IP2 Network isn’t your only option. The digital privacy landscape is filled with different tools, each taking its own approach to keeping you safe and anonymous.
VPNs and Tor have been the go-to choices for privacy-conscious users for years. But how does the IP2 Network stack up against these established players? Think of it like choosing the right security system for your home – each option offers different levels of protection and comes with its own trade-offs.

Understanding these differences becomes especially important when you’re researching dining spots in different countries, sharing travel reviews, or connecting with local food communities. Your choice of privacy tool can significantly impact both your security and your browsing experience.
IP2 vs. VPNs
VPNs work by creating a secure tunnel between your device and a remote server. When you connect to a VPN, all your internet traffic gets encrypted and routed through that server, making it appear as though you’re browsing from the server’s location instead of your actual spot.
The biggest difference between VPNs and the IP2 Network comes down to decentralization versus centralized servers. VPNs depend entirely on their company’s servers. While good VPN providers use strong encryption, your data still passes through their infrastructure. This means you’re putting complete trust in that company – and if their servers go down or get compromised, you’re left exposed.
The IP2 Network takes a completely different approach. There are no central servers to fail or betray your trust. Instead, your data flows directly between network nodes, creating a web of connections that can’t be controlled by any single entity.
Anonymity levels also differ significantly. VPNs hide your real IP address by giving you a shared one from their server pool. However, the VPN company itself can see both your real IP and your browsing activity. The IP2 Network offers much stronger anonymity because your traffic bounces through multiple encrypted tunnels across various nodes, making it nearly impossible to trace back to you.
Performance is where VPNs typically shine. Since they’re designed for speed and use direct routing through professional infrastructure, VPNs usually offer excellent browsing speeds. The IP2 Network generally performs better than Tor but can still be slower than a direct VPN connection due to its multi-hop routing system.
Both technologies mask your IP address effectively, but the IP2 Network integrates this with advanced encryption and multi-path routing for more robust protection overall.
IP2 vs. Tor
Tor has earned its reputation as the gold standard for online anonymity. It works by encrypting your data in multiple layers (like peeling an onion) and sending it through at least three volunteer-run relays before it reaches its destination.
The routing methods represent a key technical difference. Tor uses “onion routing” – wrapping data in multiple encryption layers that get peeled away at each relay. The IP2 Network uses “garlic routing,” which bundles multiple encrypted messages together and sends them through different paths simultaneously. While both provide strong anonymity, garlic routing can sometimes be more efficient at handling traffic.
Speed and latency often make or break the user experience. Tor is notoriously slow because it relies on volunteer-run relays and routes everything through multiple hops. This makes it frustrating for activities like streaming videos or downloading large files. The IP2 Network typically runs faster than Tor while still maintaining strong privacy protections, making it more practical for everyday use.
Network scope differs significantly between the two. Tor primarily focuses on letting you access the regular internet anonymously, though it also hosts hidden services. The IP2 Network creates its own internal ecosystem where both users and servers remain hidden from outside observation. While you can configure it to access the regular internet, its real strength lies in creating this anonymous overlay network.
Ease of use remains challenging for both systems. Tor has improved its user interface over the years, but it still requires some technical knowledge to use safely. The IP2 Network also has a learning curve, requiring initial setup and configuration that might intimidate casual users.
Here’s how these privacy tools compare across key features:
| Feature | IP2 Network | Tor | VPN |
|---|---|---|---|
| Privacy Level | High | High | Medium to High |
| Encryption | Excellent | Limited (at exit) | Excellent |
| Ease of Use | Moderate | Low | High |
| Decentralization | Fully Decentralized | Fully Decentralized | Centralized Servers |
| Performance Speed | Good | Slower | Excellent |
| Anonymity | Strong IP Obfuscation | Strong anonymity | Shared IPs, moderate anonymity |
The IP2 Network finds its sweet spot by offering decentralized privacy without the speed penalties of Tor or the trust requirements of VPNs. For users who need reliable privacy protection without sacrificing too much performance, it presents a compelling middle ground that’s worth considering.
Getting Started: Your Guide to Using the IP2 Network
Taking your first steps with the IP2 Network is a bit like learning to steer a new city’s food scene. At first glance, it might seem overwhelming, but once you understand the basics, you’ll find a world of possibilities that traditional internet browsing simply can’t offer.
The truth is, getting started does require a little more effort than downloading your favorite restaurant app. The IP2 Network prioritizes privacy and security over convenience, which means there’s a learning curve involved. But don’t worry – thousands of users have successfully made this transition, and with the right guidance, you can too.
Your journey begins with understanding that you’ll need specific software to connect to this decentralized network. Think of it as needing a special key to open up a private dining room. The most essential piece is an IP2 Network router application, with the I2P Router being the gold standard that most users rely on.
This router software becomes your personal gateway to the network. It manages all the complex behind-the-scenes work – creating encrypted tunnels, finding optimal routes through the network, and ensuring your data stays private as it travels from point to point.
Steps to Connect to the Network
Getting connected to the IP2 Network follows a logical progression that builds your privacy protection step by step.
Installing your router is the foundation of everything else. You’ll want to download the I2P Router from the official source and install it on your device. This software runs quietly in the background, much like how your favorite food delivery app stays ready to connect you with restaurants.
Configuring your applications comes next. Once your IP2 Network router is running, you’ll need to tell your web browser, messaging apps, and other software to route their traffic through the network’s proxy. This step ensures that your internet activity actually benefits from the privacy features you’ve just installed.
Using specialized P2P clients opens up more advanced possibilities. Applications like I2PSnark for torrenting or Tribler for decentralized file sharing are designed specifically to work within the IP2 Network. These tools understand how to communicate directly with other network nodes without leaking your real identity.
Setting up tunnels represents the more advanced tier of usage. Experienced users often configure IP-over-P2P tunnels using tools like IPOP, which creates virtual private networks that route traffic through the IP2 Network. This essentially builds a secure bridge between devices over the peer-to-peer connection.
Testing and monitoring your connection ensures everything works properly. The I2P Router includes a user-friendly interface where you can check your connection status, monitor tunnel performance, and verify that your traffic is flowing through the encrypted network as intended.
The key to success is starting simple. Use the official I2P Router GUI initially – it provides clear feedback about what’s happening with your connection. As you become more comfortable, you can explore additional applications and advanced configurations.
Practical Applications and Use Cases
Once you’re connected, the IP2 Network transforms from an abstract concept into a practical tool that improves your digital life in meaningful ways.
Secure messaging becomes possible without worrying about surveillance or data collection. Whether you’re coordinating with fellow food bloggers about a new restaurant opening or discussing sensitive travel plans, your conversations remain truly private. The network powers encrypted messaging applications that ensure your communications never pass through corporate servers that might store or analyze your words.
Anonymous browsing opens doors that might otherwise be closed. Food enthusiasts traveling in regions with internet restrictions can research restaurants, read reviews, and access culinary websites without revealing their location or identity. This capability proves especially valuable when exploring local food scenes in areas where certain content might be blocked or monitored.
Decentralized social media represents the future of online community building. Imagine food communities where recipes, restaurant reviews, and culinary discussions aren’t subject to algorithmic manipulation or corporate censorship. These platforms distribute content across network nodes rather than storing everything on vulnerable central servers.
Censorship-resistant file sharing enables direct exchange of content between users. Food photographers can share high-resolution images, cookbook authors can distribute their work, and culinary educators can exchange teaching materials without relying on cloud services that might restrict or monitor their content.
Private torrenting through I2PSnark offers a significantly more secure alternative to traditional file sharing. This application operates entirely within the IP2 Network‘s encrypted environment, preventing traffic leaks that could expose your identity or activities.
The applications extend far beyond these examples. Smart city initiatives use the IP2 Network for IoT connectivity, enterprises rely on it for secure communications, and industries from healthcare to finance explore its potential for protecting sensitive data. For food and travel enthusiasts, it represents a way to explore, share, and connect without compromising personal privacy or freedom of expression.
The Future of IP2: Benefits, Challenges, and Web3 Integration
Picture this: you’re researching hidden culinary gems in a country with strict internet restrictions, or you’re a food blogger wanting to share honest restaurant reviews without corporate interference. The IP2 Network represents more than just technical innovation – it’s about creating digital spaces where food enthusiasts, travelers, and content creators can connect authentically.
The technology stands at an exciting crossroads. Its promise of improved security and robust anonymity could fundamentally change how we find, share, and discuss our culinary adventures online. Yet like a complex recipe that needs perfecting, it faces real challenges in becoming accessible to everyday food lovers and travel enthusiasts.
What makes this particularly interesting is how well the IP2 Network aligns with the Web3 movement. Think of Web3 as the internet’s evolution toward user ownership – where your travel photos, restaurant reviews, and culinary findies truly belong to you, not to big tech companies.
Key Benefits of Adoption
The advantages of embracing the IP2 Network feel especially relevant for anyone passionate about food and travel experiences:
True decentralization means no single company controls your dining recommendations or travel content. Imagine sharing your favorite local bistro findies without algorithms deciding who sees them. The network’s resilient design ensures your content and connections remain accessible, even if traditional platforms face outages or restrictions.
Improved privacy becomes crucial when you’re exploring sensitive topics – perhaps investigating food safety issues, sharing honest reviews of powerful restaurant chains, or documenting culinary traditions in politically sensitive regions. The IP2 Network’s built-in encryption and multi-hop routing protect both content creators and readers.
Freedom of information takes on special meaning in the food world. Whether you’re accessing uncensored reviews of tourist trap restaurants, sharing authentic cultural food experiences that might challenge mainstream narratives, or connecting with local food communities in restrictive regions, censorship resistance becomes invaluable.
Improved security protects against the data breaches that have plagued major travel and dining platforms. Your restaurant preferences, location data, and personal dining habits stay truly private, reducing risks from centralized data storage.
Challenges and Limitations
However, we’d be dishonest if we didn’t acknowledge the problems ahead. The IP2 Network currently requires more technical comfort than downloading your favorite food delivery app. For food bloggers, travel enthusiasts, and restaurant owners who just want to connect and share, the initial setup can feel overwhelming.
Public awareness remains limited. Most people finding new restaurants or planning culinary trips have never heard of decentralized networks. This creates a catch-22: the network needs users to thrive, but users need to know it exists first.
Scalability concerns become real when imagining millions of food lovers sharing high-resolution photos, detailed restaurant guides, and video content of their culinary adventures. The network must handle this growth while maintaining the speed that modern users expect.
There’s also the reality that powerful privacy tools can sometimes attract misuse. Like any technology, the IP2 Network emphasizes responsible use, particularly important in food and travel communities where trust and authenticity matter deeply.
The Outlook for the IP2 Network in a Web3 World
The future looks particularly bright when we consider how the IP2 Network fits into Web3’s vision. For food and travel enthusiasts, this could mean changes in how we experience culinary findy.
Integration with DeFi could enable private transactions for exclusive dining experiences, anonymous payments to local food guides, or secure financial exchanges within culinary communities – all without revealing personal spending patterns or travel plans.
Decentralized identity systems could let food critics, travel bloggers, and culinary experts build reputation without surrendering personal data to platforms. Your expertise in Italian cuisine or knowledge of Bangkok street food becomes truly yours to control and monetize.
In the emerging metaverse, imagine virtual food tours, digital cooking classes, or immersive restaurant experiences that require secure, private communication. The IP2 Network could provide the foundation for these interactions, ensuring your virtual culinary adventures remain as private as you choose.
Perhaps most intriguingly, as quantum computing advances and threatens current encryption, the IP2 Network’s evolving security measures position it to protect food and travel content far into the future. Its AI-driven features could adapt to new threats, keeping culinary communities safe in an increasingly complex digital landscape.
The IP2 Network isn’t just another tech tool – it’s infrastructure for a more authentic, user-controlled way of sharing our passion for food and travel. As digital privacy becomes increasingly precious, technologies like this could define how future generations find their next favorite restaurant or plan their dream culinary adventure.
Frequently Asked Questions about the IP2 Network
When we talk about the IP2 Network with fellow food lovers and travel enthusiasts, we notice the same questions pop up time and again. Whether you’re a curious foodie wanting to protect your dining reviews from prying eyes or a tech-savvy traveler seeking better privacy while researching your next culinary adventure, these are the answers you need.
Is the IP2 Network legal to use?
Here’s the straightforward answer: yes, the IP2 Network is completely legal to use. Think of it like owning a high-quality kitchen knife – the tool itself is perfectly legal, but what matters is how you use it.
The IP2 Network is simply a technology designed to improve your privacy and security online. Using it for legitimate purposes is not only legal but increasingly smart in our digital world. Whether you’re securely sharing restaurant recommendations, protecting your location while researching dining spots, or communicating privately with local food communities, you’re well within legal bounds.
The line gets crossed only when someone uses any technology – including the IP2 Network – for illegal activities. Just as you wouldn’t use that kitchen knife for anything other than cooking, responsible use means following all local and international laws. We always encourage our community to use these privacy tools ethically and responsibly.
Does the IP2 Network require special hardware?
This is where the IP2 Network really shines – no special hardware needed whatsoever. You won’t need to buy expensive new equipment or completely overhaul your current setup. It’s as simple as downloading new software to improve your existing system.
The beauty lies in its software-based approach. You simply install the necessary router application (like the I2P Router) on whatever device you’re already using – your laptop, desktop, or even some mobile devices. It works seamlessly with your current internet connection, whether you’re connected to WiFi at your favorite coffee shop or using your home network to plan your next food tour.
This compatibility with existing systems means you can start exploring improved privacy without any upfront hardware investment. It’s designed to integrate smoothly into your current digital life, making the transition as painless as trying a new restaurant recommendation.
Can I use the IP2 Network with a VPN for extra security?
Absolutely, and we actually think this is a brilliant approach! Combining the IP2 Network with a VPN creates multiple layers of security – think of it like having both a strong password and two-factor authentication on your accounts.
When you layer these security measures together, you’re creating what we call a defense-in-depth strategy. Your VPN encrypts your connection first, then the IP2 Network adds its own layer of encrypted, decentralized routing on top. This means anyone trying to monitor your online activity would need to break through multiple barriers.
Here’s how it works in practice: your internet service provider only sees encrypted traffic going to your VPN server, while the VPN server sees encrypted IP2 Network traffic. This dual-layer protection makes it incredibly difficult for anyone to track your online movements, whether you’re researching hidden gem restaurants or sharing sensitive dining industry insights.
Yes, there might be a slight performance impact – your data takes a few extra hops and goes through additional encryption. But for anyone who values maximum privacy and security, especially when handling sensitive information or communicating in regions with internet restrictions, this trade-off creates a much safer online experience.
Conclusion
As we wrap up our exploration of the IP2 Network, it’s clear we’ve finded something pretty remarkable. This isn’t just another tech trend that’ll fade away next year – it’s a genuine shift toward putting you back in control of your digital life.
Think about it: every time you search for that perfect little bistro in Paris or share photos from your latest food adventure, your data travels through countless servers owned by companies you’ve never heard of. The IP2 Network changes that game completely. It creates direct, encrypted connections between users, cutting out the middlemen who’ve been collecting and selling your information.
The beauty of decentralization lies in its simplicity, even though the technology behind it is complex. When every device becomes a node in the network, there’s no single point that can fail, get hacked, or be shut down. It’s like having a conversation in a crowded restaurant – your words travel directly to your friend across the table, not through the manager’s office first.
We’ll be honest: the IP2 Network isn’t as easy to set up as downloading your favorite food delivery app. It requires a bit more technical know-how and patience. But for those who value their privacy – whether you’re a food blogger protecting your sources or simply someone who believes your dining preferences shouldn’t be anyone else’s business – it’s worth the effort.
The future looks bright for this technology. As Web3 continues to grow and people become more aware of how their data is being used, the IP2 Network offers a path forward that puts users first. It’s not about hiding from the world; it’s about choosing when and how you share your information.
For us here at The Dining Destination, understanding technologies like the IP2 Network helps us better serve our community. Whether you’re researching hidden gems in your hometown or planning a culinary journey halfway around the world, doing so securely and privately should be your right, not a privilege.
The balance between innovation and usability will continue to evolve. But one thing’s certain: the IP2 Network represents a future where technology serves us, rather than the other way around. And that’s a future worth exploring.








